SSH Attack Analysis: Identifying Hacker Origins and Frequencies
Introduction
Some time ago, I was surprised by the number of attacks my newly-enabled server was receiving. However, I never took the time to quantify them.
For these reason, in this article, I aim to start quantifying these attacks, focusing on the SSH service.
By putting realistic numbers on paper, I hope to provide a more complete view of how compromised we might be.
The Script
I’ve developed a script that identifies IP addresses that have either failed login attempts or used nonexistent usernames in an attempt to log into the server. This script scans the server logs to detect these suspicious activities, capturing the IP addresses involved in these failed authentication attempts.
Additionally, the script queries AbuseIPDB to determine the origin of these IP addresses. By doing so, it can provide insights into where these attacks are coming from, helping to map out the geographical distribution of these malicious attempts.
The script also counts the number of times each IP address has interacted with our server, giving a clear picture of the frequency and persistence of these attacks. This helps to identify the most aggressive attackers and understand the scale of the threat.
Finally, the script records all this information in a database. By storing the data, we can perform further analysis, track trends over time, and generate reports that provide a comprehensive view of the security landscape affecting our server.
Now, I’ll explain parts of the code to help you understand how it works.
- Main function
The workflow of the script can be understood by looking the main function lines
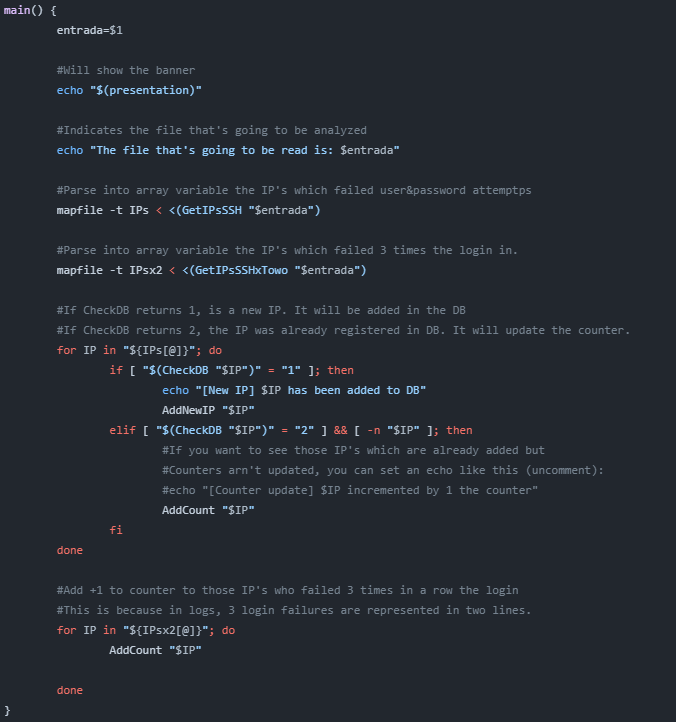
echo ”$(presentation)”: Will show the script’s banner
mapfile -t IPs < < (GetIPsSSH): will save in array variable the detected login failures due to an unknown user or bad password
mapfile -t IPsx2 < < (GetIPsSSHxTowo): Will save in an array variable those login failures that logs indicate as two times failed in one line, in order to set the correct count in the database..
for IP in ”${IPs[@]}”; do…: Inside this loop, each IP will be checked in the database to determine if it needs to be introduced or if it already exists and only the count value needs to be updated. This helps us maintain accurate final counters.
for IP in ”${IPsx2[@]}”; do…: In the SSH login procedure, when you fail the login three times in a row, the log file won’t show three different lines to warn you. Instead, this message will appear: ‘…message repeated 2 times…‘. This line is identified in the previous loop but only once, and it represents two connections. Therefore, we search for these lines and the associated IPs to update the count accordingly.
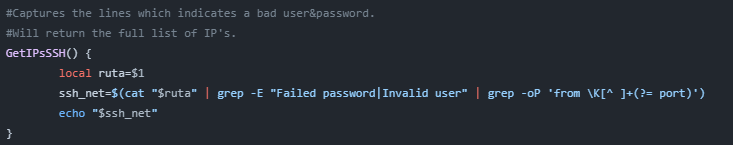
2. GetIPsSSH
This function will execute the following command to extract only the IPs that failed due to an incorrect password or unknown user:
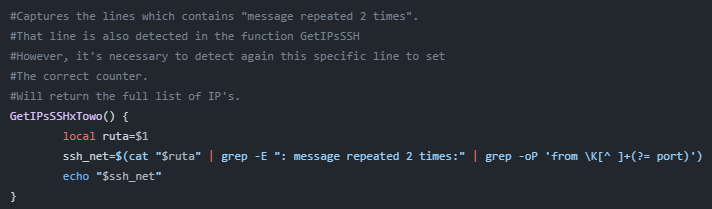
- GetIPsSSHxTowo
This function will execute the following command to extract only the IPs that had 3 login failures (which are logged as 2 lines instead of 3). The intention is to simply add +1 to the counter.
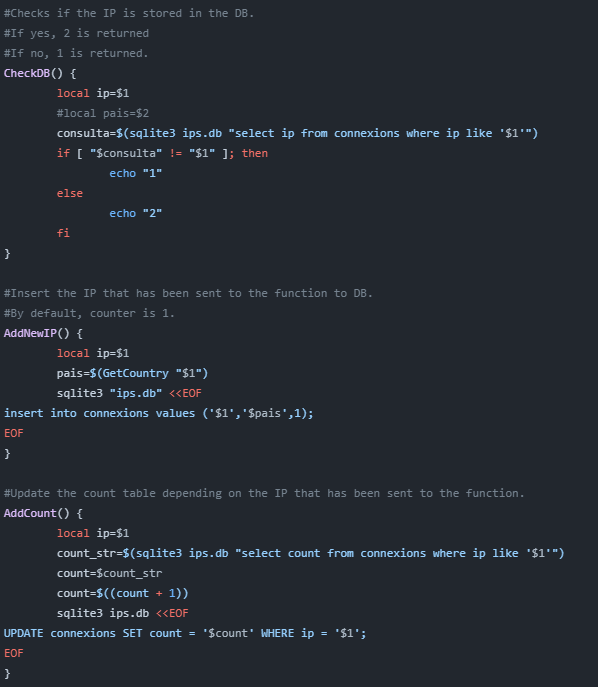
4. Check, Insert & Update values in database
This section is quite straightforward. Here’s a breakdown of what each function does:
CheckDB: Verifies if the IP exists in the database. If Returns ‘1’ if the IP is not found.
AddNewIP: Adds the IP to the database if CheckDB returns ‘1’.
AddCount: Updates the counters if CheckDB returns ‘2’, indicating that the IP already exists.
 Counter Results
Counter Results
The following table will show the top 45 countries that tryied to get access into my server.
Each number represents the counters. 1 counter = 1 login failed.
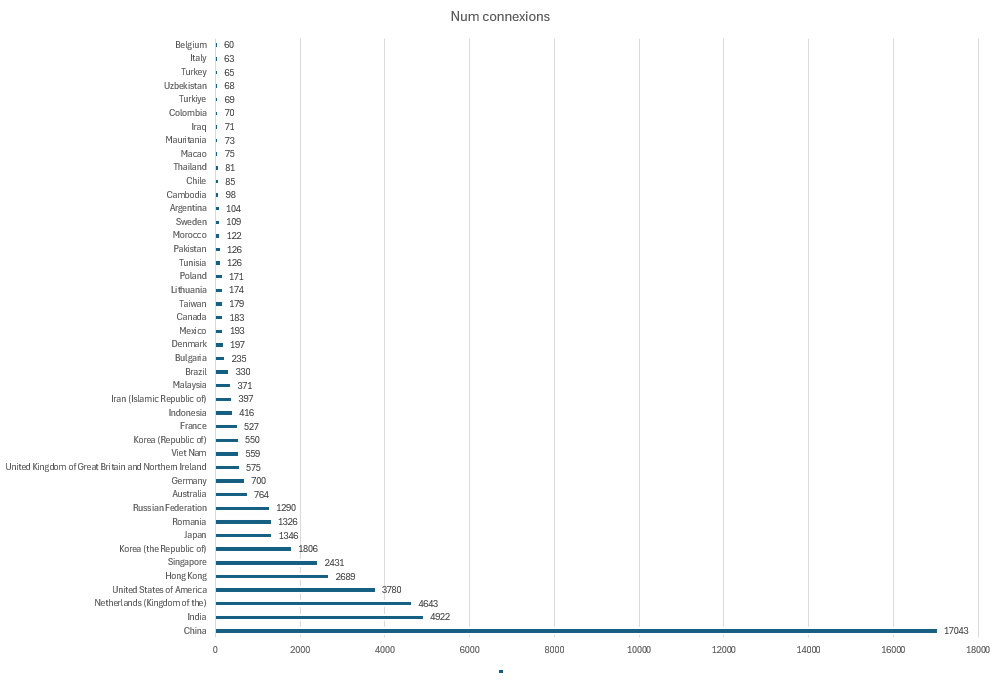
The total counter is 50097 (=50097 login failures)